Chapter 2: Azure Arc Architecture & Connectivity
Understanding the control plane, communication paths, and how Azure Arc securely connects your hybrid and multi-cloud infrastructure to Azure. We will go more in-depth in the following chapters
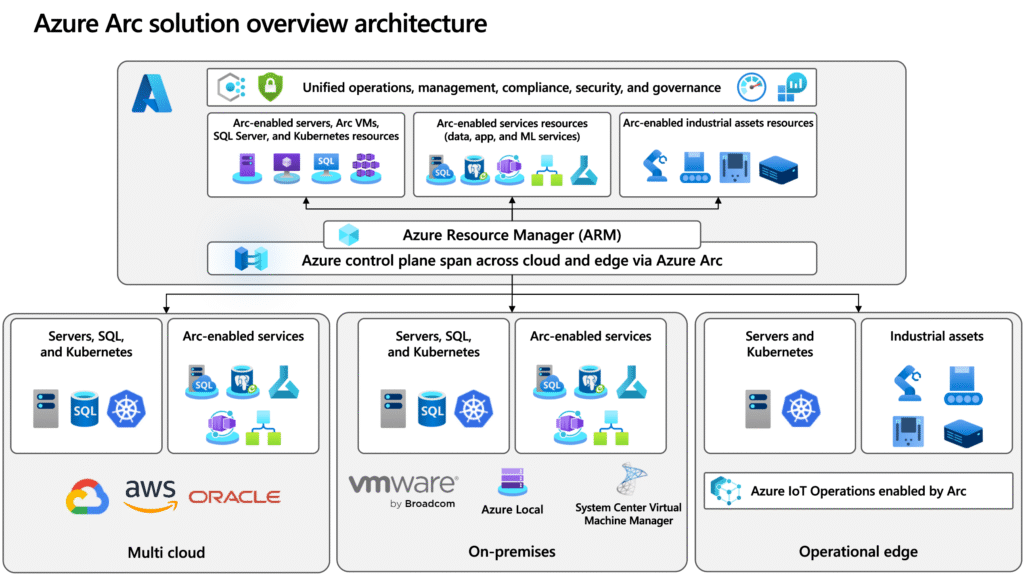
Azure Arc: a high-level view
Azure Arc isn’t a single service — it’s a framework that sits across multiple Azure components. At a high level, it consists of:
🔹 Azure Control Plane Extension
- Azure Arc leverages Azure Resource Manager (ARM) to project external resources into Azure.
- Each Arc-enabled resource appears as a first-class Azure object — with a resource ID, tags, policy scope, RBAC assignments, etc.
- This enables seamless integration with services like Azure Monitor, Defender for Cloud, and Azure Policy.
🔹 Arc Agents & Extensions
- Lightweight agents or operators run on the target resource (e.g., VM or Kubernetes node).
- These agents initiate outbound communication to Azure (no inbound ports required).
- They also manage Arc extensions — modules that add capabilities like monitoring, guest configuration, or GitOps.
🔹 Disconnected status
- The agent can handle this and a few locally services will continue to work limited !
- Example limited functionality: when the agent disconnects and doesn’t reconnect within 14 days the assignments will be deleted and not reapplied.
- What will work: Guest configuration, azure policy and arc agent logs.
- We’ll go more in detail in the next chapters..
Connectivity Models: how does azure arc connect?
Understanding Arc’s network architecture is critical for secure deployments. Here’s how the pieces connect:
🔹Outbound communication only
- All agents initiate communication to Azure over HTTPS (port 443).
- No inbound firewall changes are needed — ideal for secure, enterprise environments.
🔹Public endpoint or Private link
- By default, Arc connects to Azure’s public endpoints over the internet.
- For regulated or sensitive environments, Azure Arc supports Private Link — keeping traffic within Azure’s backbone and enhancing security.
🔹Proxy & Firewall Support
- Arc agents can be configured to use HTTP or SOCKS proxies.
- You can define proxy bypass lists for specific endpoints (e.g., metadata, identity, telemetry).
If you want to go more in depth: Connected Machine agent network requirements – Azure Arc | Microsoft Learn
Identity, Access & Security Model
Azure Arc resources inherit all the security and access features of Azure-native resources:
🔹Key security features:
- Azure RBAC: Role-based access control over all Arc resources
- Azure Policy: Enforce compliance across your fleet, including non-Azure workloads
- Managed Identities: Securely authenticate workloads to Azure services
- Microsoft Defender for Cloud: Enable threat detection across Arc-connected resources
🔹Compliance
Arc supports compliance standards like:
- CIS benchmarks
- NIST 800-53
- ISO 27001
… using Azure Policy + Arc-enabled Guest Configuration.
Identity & auth: Identity and authorization – Azure Arc | Microsoft Learn
Architecture in Practice: Lifecycle Flow
Here’s a simplified flow when you Arc-enable a resource (e.g., a Linux VM):
- Install the agent
- Authenticate to Azure (via service principal or managed identity)
- Register the resource
- Azure creates a proxy object for the machine in the specified subscription
- Agent starts telemetry and heartbeat
- You can now:
- Apply policies
- Install extensions
- Monitor and secure the resource
Scalability & Extensibility
Azure Arc is built for enterprise scale:
- Onboard thousands of resources using Azure Policy, Terraform, or automation scripts
- Use Custom Locations to group Arc resources into logical regions
- Integrate with Azure Lighthouse for cross-tenant management
Resource unified operations: Azure Arc Jumpstart
Summary
Azure Arc’s architecture is designed for scale, security, and flexibility. Whether you’re connecting 50 on-prem VMs or deploying cloud-native SQL services at the edge, Azure Arc gives you the Azure control plane everywhere.
It doesn’t matter where your workloads run — with Azure Arc, they feel like Azure-native resources.
Coming Next: Chapter 3 – Azure Arc for Servers
We’ll take a deep dive into how to onboard, manage, monitor, and secure your physical and virtual machines with Azure Arc.